Governance

Corporate Governance
We position improving management transparency, enhancing the supervising function, making decisions promptly, and ensuring compliance as our most important corporate governance tasks. We are taking steps to strengthen and enhance our corporate governance system in an effort to improve our corporate value.
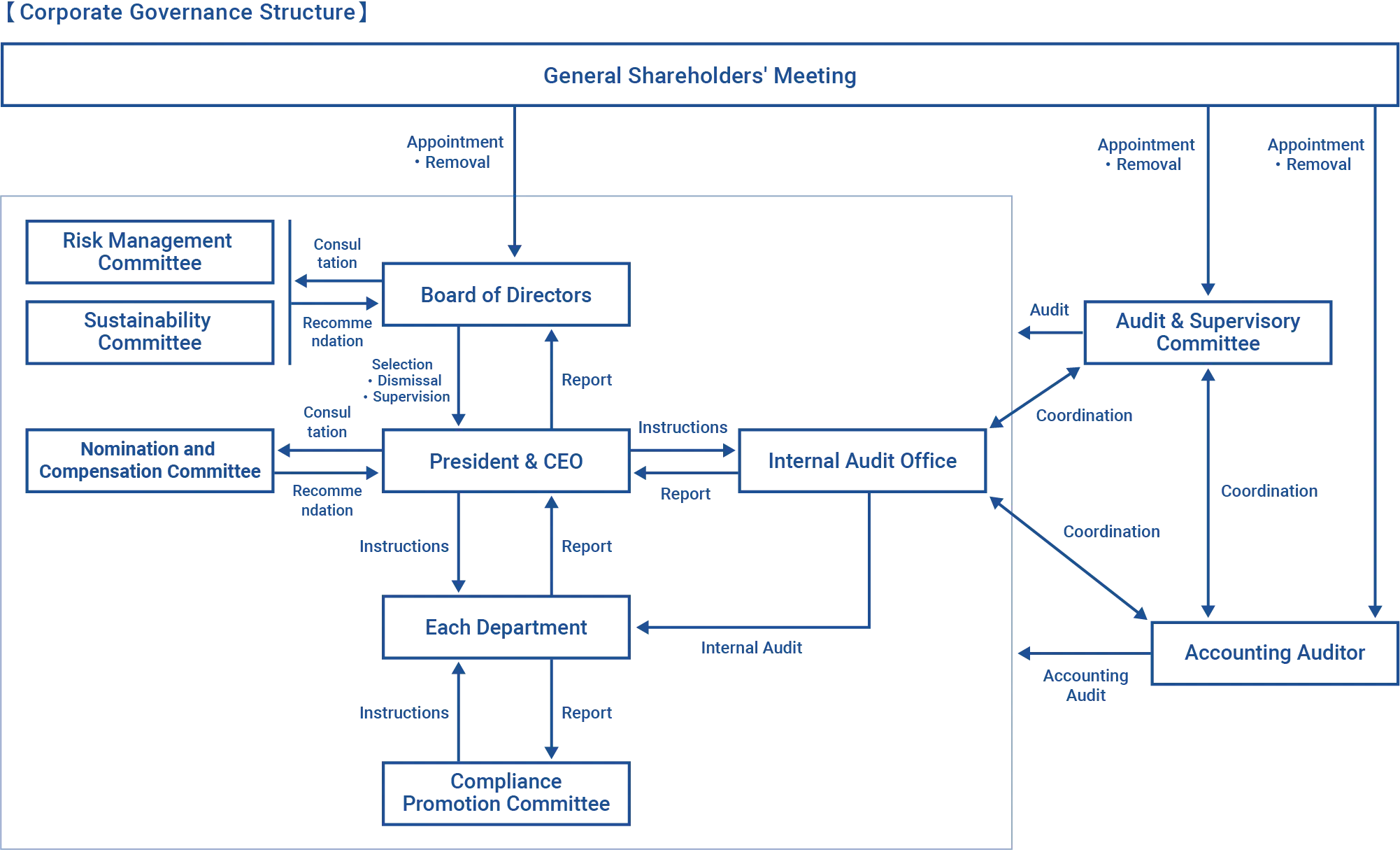
Corporate Governance Structure
We are a company with an Audit & Supervisory Committee. We have built a corporate governance structure centered on the Board of Directors, and an Audit & Supervisory Committee.
Director
By appointing six of the nine directors as independent outside directors, we are able to incorporate diverse perspectives into management and strengthen the mutual monitoring function among directors. We have set a target for highly independent outside directors, who are appropriately distanced from business execution, to constitute more than half of the total number of directors. In selecting director candidates, we aim to ensure diversity of skills and experience and, irrespective of attributes such as gender, race/ethnicity, nationality, country of origin, or cultural background, select candidates who can discharge the duties and responsibilities of a director. By having a non-executive director preside over the Board of Directors, we promote a separation between oversight and execution.
Audit & Supervisory Committee members
We have four Audit & Supervisory Committee members and all of them are independent outside directors. They audit the status of business execution by directors. At the same time, they regularly exchange opinions with other outside directors, conduct joint audits and share their results with the Internal Audit Office each other, have meetings with the auditing firm, and take other measures to examine the appropriateness and soundness of business execution in greater detail.
Internal Audit Office
Through auditing activities, it examines and evaluates our management’s business execution from the viewpoint of legality and rationality. In addition, this organization evaluates the effectiveness of our internal control system.
Nomination and Compensation Committee
To help ensure the transparency of our management, we have set up a Nomination and Compensation Committee that comprises the CEO and outside directors (two or more outside directors, who constitute the majority).The committee deliberates and reports on the details of compensation received by directors and executive officers, and the policy for determining such compensation, the policy for nominating candidates for directors excluding Audit & Supervisory Committee members, and the policy for appointing executive officers.
See our Corporate Governance Report for other details of our corporate governance.
Compliance
We set forth the following Compliance Policy for the purpose of carrying out business activities in compliance with laws, regulations, and contracts and by high ethical standards. Everyone who works for BayCurrent Consulting acts in accordance with this Policy, makes consistent efforts to live up to the trust of our stakeholders, and takes the initiatives described in this Policy, in an effort to ensure a higher level of compliance.
Risk Management
We believe that it is important to identify the risks we face or are likely to face in the future, and to take organizational, appropriate preventive measures against those risks. We take risk-hedging measures and a range of risk control initiatives.
- The Compliance Promotion Committee instructs each business division to clarify risks and report its risk management measures on a quarterly basis, in principle, in an effort to identify risks.
- Policy on addressing material management risks and other matters that are important from the perspective of risk management are fully discussed at various meetings. In addition, matters that are especially important are reported at Board of Directors’ meetings and appropriate measures are taken against them as necessary.
- In the case of a serious matter related to business activities, we hold an extraordinary meeting of the Compliance Promotion Committee and respond to the matter promptly, so as to build a framework for preventing and containing damage and losses.
Risk Governance Framework
We have established a governance framework centered on the Board of Directors to appropriately manage the diverse risks inherent in our management and business activities. In particular, based on the Three Lines of Defense model, we clearly delineate risk management responsibilities to ensure sound and sustainable business operations.
Risk oversight at the Board level
The Board of Directors bears ultimate responsibility for risk management and oversees risks across the enterprise with an appreciation of their materiality. The Board of Directors has also established a specialized committee on risk management, which receives and deliberates regular reports on material risks at least once a year. Through these arrangements, we ensure transparency and accountability in management decision-making.
Risk governance at the operating level (Three Lines of Defense model)
First line: Ownership of operational risks
Business units and frontline employees directly manage and address risks in day-to-day operational processes. Risk owners (e.g., risk managers, unit heads) are clearly designated and bear responsibility for executing risk mitigation.
Second line: Risk management and compliance oversight
Under the Board of Directors’ policies, the Risk Management Committee sets standards and rules and oversees adherence in coordination with business units. The second line operates independently of the CEO and reports to the Board.
Third line: Independent audit function
From an independent position reporting directly to the Board of Directors, the internal audit department periodically verifies and assesses evaluates the effectiveness of the risk management and compliance framework. In doing so, it provides objective assurance on the alignment of each unit’s activities with management policies and risk appetite, and offers recommendations for improvement.
Basic policy on risk management
To address uncertainties across diverse domestic and international business environments, we foster an effective risk culture and enforce risk management across the entire organization. We position risk management not merely as a compliance response, but as a foundational element of management to ensure long-term sustainable growth and financial stability.
Risk review process
We identify and assess business-related risks and formulate risk mitigation measures. In our reviews, we conduct quantitative and qualitative evaluations that combine likelihood and impact, and we set the risk appetite in accordance with our framework.
Identified risk (i): Cybersecurity risk
Impact: A material risk of eroding customer trust due to leakage of confidential information and operational shutdowns
Likelihood: Medium or higher, due to the rapid sophistication of attack techniques
Risk appetite: As a basic policy, we tolerate no attacks under any circumstances and require continuous strengthening of our defenses.
Mitigation measures: Deployment of a multilayered defense system and rigorous information security training for all employees
Identified risk (ii): Talent acquisition and development risks
Impact: Decline in the quality of consulting services and loss of growth opportunities
Likelihood: High, due to intensifying competition for hires with competitors
Risk appetite: Moderate (within a range that does not impede business growth)
Mitigation measures: Diversification of recruitment processes; ongoing training programs for leaders; improvement in retention by promoting flexible work arrangements
BCP
We understand that ensuring business continuity in the event of a disaster is an important task. In particular, we believe that protecting the safety of employees and their families by giving it top priority, eliminating employees’ anxieties arising from the disaster, and resuming normal living activities as soon as possible are the most important tasks that are essential for business continuity. Based on this belief, we take the following initiatives.
- When a disaster such as a major typhoon and an earthquake has occurred, we confirm the safety of all employees immediately. Moreover, we tell employees to give top priority to their own safety instead of work when a disaster has occurred or a large-scale blackout, disruption of public transport services, or other incident has been caused by a disaster. We also keep emergency food and other supplies in stock at our offices.
- We own a backup data servers, which enables us to continue business even if the main servers become inoperable due to a disaster or similar event.
Information Security
We believe that firmly maintaining a high level of corporate ethics related to information security and protecting our clients’ information assets from every threat are important tasks for continuing to contribute to our clients’ sustainable development. We have therefore established an Information Security Policy to ensure appropriate protection of information assets.
We also understand that our important management tasks include not only ensuring that we do not take our trade secrets and personal information out of our offices inappropriately but also not collecting or utilizing information illegally in driving our business or supporting client companies. We therefore request each employee to pledge not to, and we instruct them not to, bring in important information such as trade secrets and personal information from other companies, excluding information obtained legally from clients and partner companies in the process of providing consulting services.
For the handling of personal information in particular, we have established a Privacy Policy.
Initiatives for ensuring information security
We take the following initiatives to ensure information security.
Security system establishment
- To ensure the proper and secure management of information and information systems, Baycurrent, Inc., along with Baycurrent Consulting, Inc. and Baycurrent Technology, Inc., have obtained certification for the international standard for Information Security Management Systems (ISMS) (ISO/IEC 27001) and has established an information security management system that conforms to this standard.
- We take risk-based safety measures for information systems that we manage. Above all, for information systems used to handle confidential information (including company information, client information, and personal information), we regularly make a vulnerability assessment to clarify their inherent risks and take action including system repair, thus keeping them robust.
- For PCs that we use for business, we restrict the use of external storage media, prohibit access to websites not needed for work, and take other steps to prevent leaks of confidential information and other incidents.
Thorough education and dissemination
- In each project team that provides consulting services to our clients, we assign an information security manager, who guides and supervises all members so that they will observe laws, regulations, and rules related to information security.
- We provide all employees with information security training (including the management of privacy information) when they join us and at least twice each year, thus informing them thoroughly of regulations and other rules that our employees should observe.
- We issue a security report every month and deliver it to each employee to raise their awareness of information security and provide them with relevant knowledge.
Establishing security requirements for third parties
We establish and apply information security requirements for third parties, such as suppliers, through contracts and other relevant agreements.
In FY2024, our company had no major compliance violations (including incidents related to the handling of customers’ personal information) requiring external disclosure.
Information security risk
Impact: High (potential for significant impact on business operations)
Likelihood: Medium (occurs roughly once every few years)
Risk recognition
The internet has become pervasive as a social infrastructure, and we now live in an era in which information can spread instantaneously. While such technological advances have increased convenience and expanded the user base, the risk of information leaks due to unauthorized external access, such as cyberattacks, has grown, and the importance of information security is being strongly scrutinized across society.
In particular, in the information services industry, where confidential customer information is frequently handled, more sophisticated security measures and rigorous employee training are required.
Risk mitigation measures
To ensure information security, we are undertaking the following initiatives.
-
Establishment of a security system
We have established an information security management system that conforms to ISO/IEC27001, an international standard for information security management systems (ISMS).
We take risk-based safety measures for information systems that we manage. In particular, for information systems used to handle confidential information (including company information, client information, and personal information), we regularly make a vulnerability assessment to identify their inherent risks and take action including system repair, in order to maintain robust sytems. -
Internal audits of the information security management system
We have established an information security management framework and operate it in conformity with international certification standards.
To assess the effectiveness of this framework and drive continuous improvement, we conduct periodic internal audits and report the results to the Board of Directors and the Audit & Supervisory Board.
In internal audits, in addition to checking compliance with internal information security policies and related rules, we objectively verify the implementation status of technical and organizational measures based on risk assessments. Where issues are identified during audits, we take corrective measures as necessary to maintain and enhance information security. -
As countermeasures against cyberattacks, we implement system defenses using a range of security devices and controls, including antivirus (malware) software, EDR, data encryption, firewalls,WAF, and behavior-based malware protection.
Recognizing that cyberattackers hold an inherent advantage and that system-level defenses alone are insufficient, we also focus on building our incident response framework. Concretely, we gather, assess, and share information on vulnerabilities and attack techniques and, as preventive activities, take organized, timely, and appropriate measures.
In addition, to strengthen our readiness for potential cyberattacks, we provide ongoing education and training such as cyber incident response drills and hands-on exercises using spear-phishing emails.
Impact in the event of an incident
In the event of an information leak, we could face claims for damages from customers and others, and suffer a loss of social credibility that may adversely affect our business performance.
Consultation services, tax affairs, and
countermeasures against anti-social forces
Anti-Corruption Measures
Under the supervision of the Board of Directors, as an important activity to thoroughly enforce compliance, we are working on the prevention of corrupt acts by conducting awareness-raising and education on matters such as anti-bribery and the Antimonopoly Act, alongside establishing rules and regulations.
To comply with anti-bribery laws and this policy, we conduct continuous education and training, and administer tests twice a year to all employees, to ensure awareness of the compliance policy.
- *In FY2025 (the current year), there have been no employees who have committed serious violations of the anti-corruption policy or were convicted of crimes related thereto. Also, there have been no employees who were disciplined or dismissed in connection with such matters.
-
*In FY2025 (the current year), there have been no fines, penalties, or settlement payments related to corrupt acts.
In addition, we are not currently making political contributions.
Consultation services for handling legal violations and misconducts
Within the company, we have established multiple consultation services related to the work environment and harassment, and have also established the “Compliance Promotion Committee Secretariat” as an internal reporting service that allows anonymous reporting. We are working to prevent and resolve various compliance issues that arise in the workplace, including legal violations, misconduct, corrupt acts, and human rights issues such as harassment.
In addition to these various internal services, we have also established a consultation service with an external lawyer that employees can consult directly. Information on how to use these consultation services is made available to all employees via our intranet portal.
We protect whistleblowers by prohibiting any disadvantageous treatment, such as dismissal or contract termination, on the grounds of making a report. Reports are handled appropriately as confidential information, and anonymous reporting is also available. After fact-finding investigations, we respond promptly and implement measures to prevent recurrence, following the process below.
a) Report received by the Compliance Promotion Committee Secretariat → b) Reporting to officers → c) Assignment of a responsible person → d) Response by the responsible person (e.g., interviews with the individual concerned and related parties)
Our views and framework on tax affairs
Our company regards increasing management transparency, strengthening supervisory functions, accelerating decision-making, and ensuring compliance as the most important issues in terms of corporate governance.
We also believe it is important to increase transparency with regard to tax payments, adhere to the tax laws of each country and region, and standards published by international organizations, strive to maintain and improve tax compliance, and pay taxes appropriately.
The Chief Financial Officer (CFO) issues and directs the basic policy regarding the proper fulfillment of the Company's tax obligations and the optimization of tax expenses, and oversees the implementation of such policy.
The Corporate Department works with relevant departments to carry out tax-related tasks under the overall direction of the CFO.
Our policy on dealing with anti-social forces
As a corporation with social responsibilities, we have established the following basic policy and observe it to prevent damage from organized crime groups and other anti-social forces.

